I think you have already noticed that recently it has become much more difficult to hide your online activity on the network. However, few people know about the existence of Deep Packet Inspection (DPI) technology, which is used by Internet service providers, governments and corporations to monitor your Internet traffic. Fortunately for us, DPI can be bypassed using a proxy, but first, let’s figure out what DPI is and what it comes with.
What is Deep Packet Inspection (DPI)?
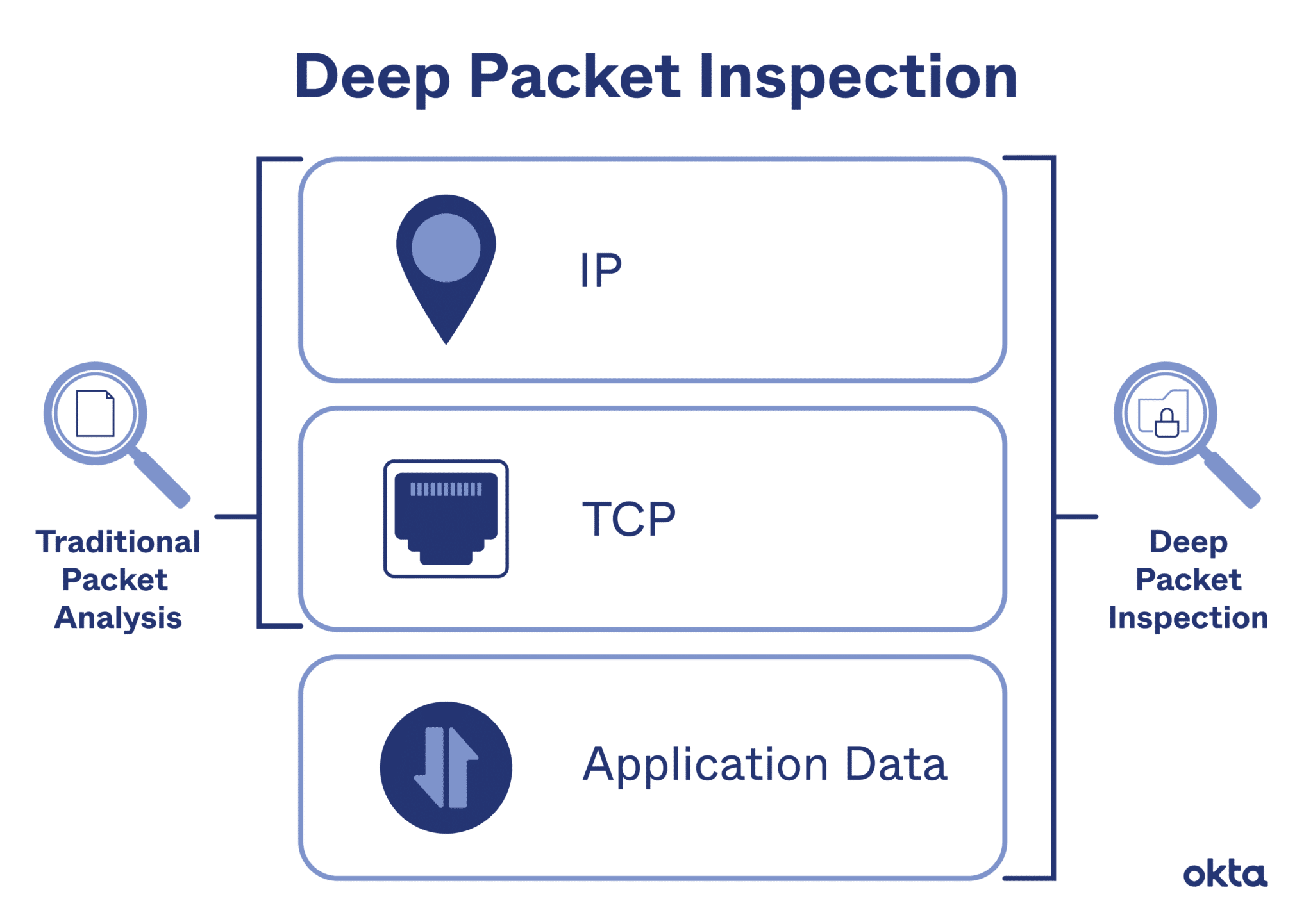
The DPI system, or DPI (deep packet inspection), works as a top-notch spy that carefully analyzes your Internet traffic, checking everything from your browser history to the applications you use. DPI is used for legitimate purposes such as network management and security, but can also become a tool for surveillance and censorship. Therefore, it is important to know how to bypass DPI and maintain your privacy and freedom online.
Proxy vs DPI
Proxy servers act as intermediaries, sending Internet requests on your behalf. This means that DPI sees their IP address, not yours. Each type of proxy has its own unique features and weaknesses:
Residential Proxies
Residential servers are real chameleons. They use the IP addresses of real users allowing your requests to fit harmoniously into regular user traffic. Thanks to this camouflage, DPI systems cannot detect them. If you need to pass for a regular user, resident ones are perfect for this purpose. However, they are slower and more expensive than other servers, so they are best used when you need to stay under the radar.
Data Center Proxies
Data center servers are fast and efficient. They are supplied by data centers and provide high-speed connections and powerful performance. These servers are great for tasks that require fast and intensive work, such as bulk data collection. But here’s the catch: because they come from large data centers, they are easier to detect, so DPI systems often detect their presence. It is better to use data center servers for tasks where connection speed is a priority, and minor suspicions of proxy activity will not harm.
SOCKS5 Proxies
Unlike previous intermediaries, SOCKS5 servers offer an additional level of security through full encryption. This means that they not only mask your IP address, but also provide encryption for the data you send and receive.
SOCKS5 proxies can handle any type of traffic other than web traffic. They are especially useful for P2P exchanges or bypassing firewalls. However, setting them up can be more complex and can slow down your connection due to the additional encryption. These proxies show the best performance in tasks related to the processing of confidential data or when bypassing strict firewalls.
When choosing a mediator, keep your goal in mind. What is more important to you – speed or anonymity? Your choice should suit your specific needs. It’s about finding the right balance between anonymity, speed and security.
How to Use a Proxy to Bypass DPI?
Now let’s talk about rotating proxies. They regularly change IP addresses, which prevents DPI systems from tracking your online activities. To enhance the effect, SSL/TLS encryption is used – even if DPI can detect the request, it will only see nonsense. Tech-savvy users can optionally implement SSH tunnels, which hide traffic in encrypted tunnels. Here are step-by-step instructions for bypassing DPI!
Step 1: Setting up a Proxy With IP Rotation
Choose a reliable provider that offers a large pool of IP addresses. Configure routing of your web requests through IP rotation proxies. This can usually be done in the web browser settings or through the provider’s personal account. Check your setup. Make a web request and check if your IP address changes.
IP rotation proxies are ideal when you need to perform tasks without leaving behind a permanent IP trail, such as web scraping or accessing geo-restricted content.
Step 2: Implement SSL/TLS Encryption
Make sure your web requests are sent over HTTPS, which is the basic form of SSL/TLS encryption. To enhance your security measures, use a proxy that offers SSL/TLS encryption for all traffic passing through it. Regularly renew SSL certificates and keep encryption protocols up to date to reduce detection risks.
SSL/TLS encryption is, in fact, critical for ALL online activities, especially when processing sensitive data or conducting transactions.
Step 3: Create SSH Tunnels
Set up an SSH server or find a service that offers SSH tunneling. Configure your device to establish an SSH connection to the server. This will create a secure tunnel for your internet traffic. Route your web traffic through this tunnel. You may need special software or browser extensions to route your traffic into the SSH tunnel.
SSH tunnels are ideal for advanced users who need an extra layer of security, especially when accessing sensitive systems or working on sensitive projects.
Combining Proxies With Other Tools
For more reliable protection, proxies can be combined with VPN and Tor. A VPN encrypts your internet connection, while Tor redirects traffic through multiple nodes. Let’s take a closer look at these two approaches.
Proxy + VPN
- How it works: When you combine a VPN with a proxy, your internet traffic goes through the proxy first and then through the VPN. This combination double masks your IP address and encrypts your data. As a result, DPI makes it twice as difficult for systems to track and intercept your online activity.
- Setting: First connect to your proxy server. Once you are connected, activate the VPN. Make sure both tools are running smoothly and check your IP address to confirm changes.
- When to use: This combination is suitable for those who need high connection speeds, a specific location, and encryption to access sensitive content or services that require a specific regional IP.
Proxy + Tor
- How it works: Here, a proxy provides an initial layer of IP address masking before your traffic hits the Tor network, which in turn routes it through multiple nodes. This ensures anonymity at the entry node, since the Tor entry node will see the proxy’s IP address and not your real IP.
- Setting: First, configure your device to connect to a proxy server. Then launch your browser or Tor. Your traffic will now pass through the server before entering the Tor network.
- When to use: This combination has the advantage of anonymity, so it is most suitable for journalists and activists who work in highly restricted conditions.
Finally
Tools by themselves are not sufficient to maintain anonymity on the Internet. It is important to use them wisely in order to achieve real results. Now you know all the strategies for keeping your digital footprint invisible. Learn, experiment, and most importantly, continue to advocate for a more private and secure internet for everyone!





