Proxy servers play a pivotal role in digital communications, acting as intermediaries between client machines and backend servers. Their primary functions encompass enhancing security measures, streamlining administrative control, and optimizing caching services. In the realm of personal computing, these servers are instrumental in safeguarding user privacy and facilitating anonymous web browsing. It’s important to note that the utilization of proxy servers spans a wide spectrum, encompassing both legitimate and illegitimate purposes.
Detailed Insight into Forward Proxy Servers
Defining a Forward Proxy Server
A forward proxy server, commonly referred to as a proxy, web proxy, or proxy server, positions itself at the forefront of a cluster of client machines. Its core function is to mediate requests from these clients to various internet sites and services. Essentially, the forward proxy acts as an intermediary, receiving client requests and then communicating with web servers on their behalf. This process is akin to a middleman’s role in transactions.
Illustrative Example of Forward Proxy Communication
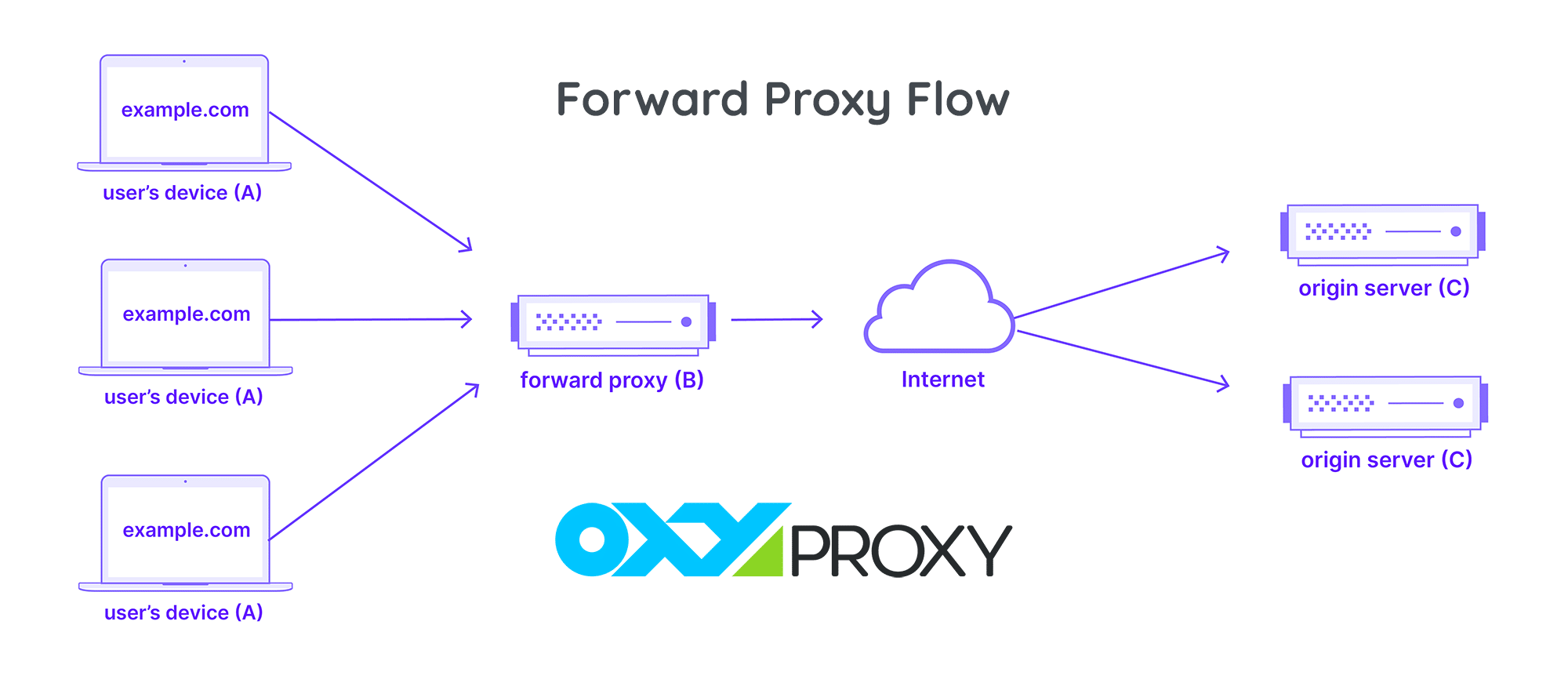
Consider a scenario involving three entities in a typical forward proxy setup:
- Computer A: Represents the user’s home computer.
- Computer B: The forward proxy server.
- Computer C: The server of a website, where the website’s data resides.
In a standard internet communication model, Computer A directly interacts with Computer C. The client (A) sends requests to the origin server (C), which in turn responds directly to the client. However, in the presence of a forward proxy, Computer A channels its requests to Computer B (the proxy). Subsequently, B forwards these requests to C, and the responses from C are relayed back to A through B.
Reasons for Utilizing a Forward Proxy
- Circumventing Restrictions: To bypass state or institutional browsing restrictions, individuals and organizations can employ forward proxies. This approach allows users to connect to the internet via the proxy server, avoiding direct access to restricted websites.
- Content Filtering and Access Control: Forward proxies are effective tools for content filtering and controlling web access. For instance, educational institutions might use them to prevent students from accessing certain websites by rerouting internet traffic through a proxy with restrictive settings.
- Online Anonymity and Identity Protection: In regions where online dissent can lead to severe repercussions, forward proxies offer a veil of anonymity. By masking their IP addresses with those of the proxy servers, users can post sensitive or politically charged content online with a significantly reduced risk of being traced.
The Role of Reverse Proxies
Contrasting with forward proxies, reverse proxies are servers that are positioned in front of web servers, primarily handling incoming client requests. The significant roles of reverse proxies include bolstering security, enhancing performance, and improving the reliability of backend servers. They act as a shield for web servers, managing and directing client requests effectively. This setup not only ensures better security but also contributes to efficient load balancing and faster content delivery, leading to an improved user experience.
In summary, both forward and reverse proxies serve crucial roles in internet communications. Forward proxies act as gateways for client requests, providing anonymity and bypassing restrictions, while reverse proxies protect and optimize the performance of web servers. Understanding the distinct functionalities and applications of these proxies is essential for effectively leveraging their capabilities in various computing environments.
Elucidating the Distinctiveness of Reverse Proxies
The Core Concept of a Reverse Proxy
A reverse proxy stands as a guardian at the forefront of one or more backend servers, essentially intercepting requests from various clients. This architectural setup is in stark contrast to a forward proxy, which positions itself in front of clients instead.
Operational Mechanics of a Reverse Proxy
In a typical internet interaction involving a reverse proxy, client requests intended for the origin server of a website are initially captured by the reverse proxy server. This server, situated at the network’s edge, acts as an intermediary. It forwards these requests to the origin or backend servers, receives their responses, and then relays these responses back to the clients. This process ensures that the direct communication between the clients and the origin servers is effectively masked.
Delineating the Differences from Forward Proxies
The nuances that differentiate forward and reverse proxies are subtle yet significant. A forward proxy acts as a shield in front of a client, ensuring that no backend server directly interacts with that specific client. Conversely, a reverse proxy serves as a protective layer in front of an origin server, preventing any direct communication between clients and that server.
An Illustrative Scenario
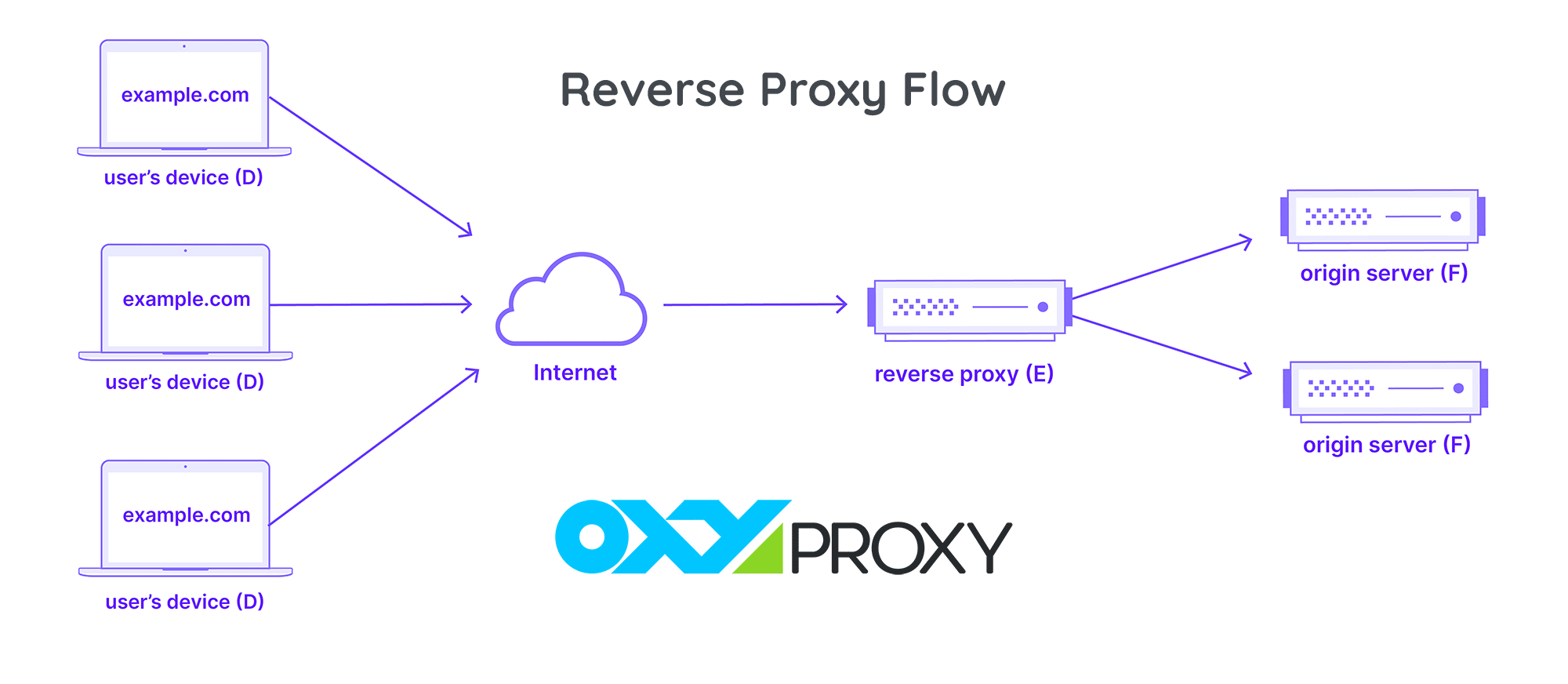
To further clarify this distinction, let’s label the entities involved in a reverse proxy setup:
- Computer D: Represents numerous users’ home computers.
- Computer E: The reverse proxy server.
- Computer F: One or more origin servers.
In a standard scenario without a reverse proxy, requests from Computer D would be sent directly to Computer F, and the responses from F would be returned directly to D. However, in the presence of a reverse proxy, the dynamics change. Here, all requests from D are initially directed to E (the reverse proxy). E then forwards these requests to F and receives responses from it. Subsequently, E passes the appropriate responses back to D.
The Significance of Understanding These Differences
Grasping the distinction between forward and reverse proxies is crucial, especially in contexts where the optimization of network performance, security, and data privacy is paramount. While both types of proxies serve to mediate internet traffic, their roles and positions within the network infrastructure differ fundamentally. Reverse proxies primarily focus on protecting and managing traffic to and from backend servers, thus playing a vital role in load balancing, security enhancement, and efficient content delivery. Understanding these differences enables network administrators and IT professionals to select and implement the appropriate proxy solution based on their specific operational needs and objectives.
Implementing a Reverse Proxy: Options and Strategies
Custom Reverse Proxy Development
For businesses seeking a high level of customization and control, developing a bespoke reverse proxy solution is a viable option. This approach, however, involves considerable investment in several areas:
- Software Engineering: Crafting a custom reverse proxy requires substantial expertise in software development, particularly in network and security protocols. This process entails designing, coding, testing, and maintaining the proxy software.
- Hardware Engineering: In addition to software, a custom reverse proxy solution demands robust hardware infrastructure. This infrastructure must be capable of handling high traffic volumes, ensuring reliability and uptime.
- Financial Commitment: The combined costs of software and hardware development, along with ongoing maintenance and upgrades, constitute a significant financial investment. Businesses must allocate funds not just for the initial setup but also for the long-term operational expenses.
Leveraging Content Delivery Network (CDN) Services
An alternative to building a custom reverse proxy is to utilize a Content Delivery Network (CDN) service. CDNs offer a more straightforward and cost-effective means to implement reverse proxy capabilities:
- Ease of Implementation: CDNs are designed to be user-friendly and require minimal setup time compared to custom-built solutions. They often provide intuitive interfaces and tools for easy configuration and management.
- Cost-Effectiveness: By subscribing to a CDN service, businesses can avoid the hefty upfront costs associated with developing and maintaining a custom reverse proxy. CDNs typically operate on a subscription model, offering scalable pricing based on usage.
- Built-In Features: CDN services come equipped with a range of features that enhance website performance and security. These include global content distribution, load balancing, DDoS protection, and caching mechanisms.
- Scalability and Reliability: CDNs are inherently designed to handle large volumes of traffic and provide high availability. Their distributed nature ensures that content is delivered quickly and reliably to users worldwide.
- Support and Maintenance: Subscribing to a CDN service includes access to technical support and automatic updates, ensuring that the reverse proxy functionality remains up-to-date with the latest security and performance enhancements.
Choosing the Right Approach
Deciding between a custom reverse proxy solution and a CDN service depends on various factors, including the specific needs of the business, available resources, technical expertise, and budget considerations. While a custom solution offers more control and customization, a CDN service provides ease of use, cost efficiency, and immediate access to advanced features without significant upfront investment. Businesses must carefully evaluate their priorities and constraints to determine the most suitable approach for implementing a reverse proxy in their network infrastructure.





