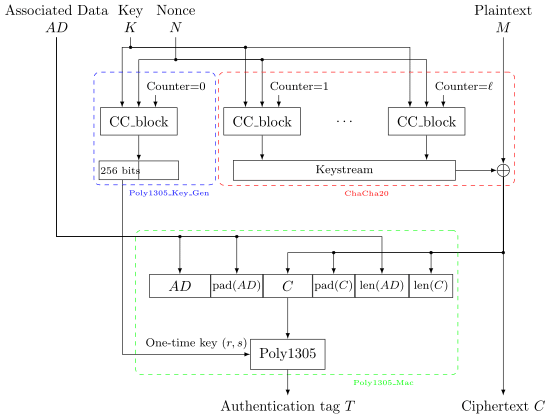
ChaCha20 is a widely recognized stream cipher and a symmetric encryption algorithm known for its security and speed. It was developed by Daniel J. Bernstein in 2008 as part of the Salsa20 family, with the primary goal of providing a robust and efficient encryption mechanism for various applications. ChaCha20 is commonly used in secure communications, including internet protocols and VPNs, due to its ability to offer both security and performance benefits.
The history of the origin of ChaCha20 and the first mention of it
ChaCha20 originated as an improvement over the Salsa20 stream cipher, which was also designed by Daniel J. Bernstein. The main motivation for creating ChaCha20 was to increase diffusion per round and boost security without sacrificing speed. ChaCha20’s design process was completed in 2008, and it was first publicly mentioned in Bernstein’s paper titled “ChaCha, a variant of Salsa20” in 2008.
Detailed information about ChaCha20. Expanding the topic ChaCha20
ChaCha20 is a stream cipher that generates a stream of pseudo-random bits based on a secret key and a unique 64-bit nonce. It uses a 256-bit key, providing a high level of security against brute-force attacks. One of its essential features is the ability to efficiently compute the encryption stream, making it highly performant in various applications.
The algorithm operates on a 4×4 matrix, initially seeded with constants, key, and nonce. It performs a series of 20 rounds of operations, mixing the data to produce the final stream. The 20-round design enhances diffusion and ensures the security of the cipher. Moreover, ChaCha20 avoids common cryptographic pitfalls like timing attacks and side-channel attacks, making it a robust choice for encryption.
The internal structure of ChaCha20. How ChaCha20 works
ChaCha20’s internal structure can be divided into the following key components:
- State Matrix: A 4×4 matrix that holds 16 32-bit integers, derived from the key, constant values, and nonce.
- Initialization: The cipher is initialized with a 256-bit secret key, a 64-bit nonce, and a 32-bit block counter. This unique combination ensures that the keystream is different for each encryption operation.
- ChaCha20 Quarter Round: This is the basic building block of the cipher. It consists of a series of bitwise operations and additions, designed to thoroughly mix the data and introduce diffusion.
- Rounds: ChaCha20 performs 20 rounds of ChaCha20 Quarter Round operations on its state matrix to generate the encryption stream.
- Keystream Generation: The final state matrix is converted into the encryption keystream, which is then XORed with the plaintext to produce the ciphertext.
Analysis of the key features of ChaCha20
ChaCha20’s design and characteristics offer several key benefits:
- Security: With a 256-bit key, ChaCha20 provides a high level of security, making it resistant to brute-force attacks.
- Performance: ChaCha20’s efficient implementation allows for fast encryption and decryption, making it suitable for real-time applications and high-speed data transmission.
- Flexibility: It supports various nonce values, allowing it to generate unique keystreams for different encryption operations with the same key.
- Resistance to Attacks: ChaCha20 is designed to be resistant to timing attacks and side-channel attacks, enhancing its overall security.
Types of ChaCha20
ChaCha20 has a few variations with different nonce sizes, primarily for specific use cases. The most common types include:
| ChaCha20 Variant | Nonce Size (bits) |
|---|---|
| ChaCha20 | 64 |
| ChaCha20-IETF | 96 |
| ChaCha20-Poly1305 | 64 |
| ChaCha20-Poly1305-IETF | 96 |
ChaCha20 can be used in various scenarios to provide secure communication and data protection. Some common use cases include:
- Secure Communication Protocols: ChaCha20 is used in TLS/SSL cipher suites to secure web communications, ensuring privacy and data integrity.
- VPN Encryption: Many Virtual Private Network (VPN) providers implement ChaCha20 to secure data transmission between the client and the server.
- Disk Encryption: ChaCha20 is suitable for full-disk encryption, protecting sensitive data on storage devices.
- Secure Messaging: ChaCha20 can be utilized to encrypt instant messaging and email communications, safeguarding sensitive content from unauthorized access.
Potential problems related to ChaCha20 usage might include:
- Nonce Reuse: Reusing the same nonce with the same key compromises the security of the encryption. Using unique nonces for each encryption operation is essential.
- Key Management: Proper key management practices are crucial to maintaining the security of encrypted data.
- Implementation Issues: Flawed or vulnerable implementations of ChaCha20 can lead to security vulnerabilities.
- Cryptanalysis Advances: As with any cryptographic algorithm, future advances in cryptanalysis could potentially weaken ChaCha20’s security.
To address these issues, it is essential to follow best practices for cryptographic key management, choose secure and well-vetted implementations, and stay informed about any potential vulnerabilities or updates related to ChaCha20.
Main characteristics and other comparisons with similar terms in the form of tables and lists
| Characteristic | ChaCha20 | AES |
|---|---|---|
| Key Size | 256 bits | 128, 192, or 256 bits |
| Block Size | 512 bits (64 bytes) | 128 bits (16 bytes) |
| Security Strength | High | High |
| Performance | Fast | Fast |
| Key Schedule | Not required | Required |
| Resistance to Timing Attacks | Yes | Yes |
| Resistance to Side-Channel Attacks | Yes | Yes |
| Adoption and Popularity | Increasingly Popular | Widely Adopted |
As technology advances and security threats evolve, ChaCha20 is likely to remain relevant due to its combination of security and performance. Its resistance to side-channel attacks and efficient implementation makes it an attractive choice for many applications.
Moreover, with the increasing demand for secure communications and data protection, ChaCha20 is expected to see continued adoption in various fields, including web communication, VPN services, and mobile applications.
How proxy servers can be used or associated with ChaCha20
Proxy servers play a vital role in securing internet traffic and enhancing privacy. By integrating ChaCha20 encryption into proxy servers, they can offer an additional layer of protection for users. When users connect to a proxy server that uses ChaCha20 encryption, their data is securely encrypted before being forwarded to the destination server. This ensures that sensitive information remains confidential during transmission, reducing the risk of eavesdropping and unauthorized access.
Proxy servers can leverage ChaCha20’s efficiency to provide fast and secure data encryption for a seamless user experience. Moreover, ChaCha20’s resistance to timing attacks and side-channel attacks makes it well-suited for deployment in proxy server environments.
Related links
For more information about ChaCha20, encryption algorithms, and related topics, you can explore the following resources:
- ChaCha, a variant of Salsa20 – Paper by Daniel J. Bernstein
- The Salsa20 Family of Stream Ciphers – eSTREAM Project
- ChaCha20 and Poly1305 for IETF Protocols – RFC 8439
- Understanding Cryptography – A Textbook by Christof Paar and Jan Pelzl
By studying these resources, you can gain a deeper understanding of ChaCha20 and its significance in the realm of modern encryption.