SOCKS5 is a widely used proxy protocol that facilitates secure and efficient communication between clients and servers over a network. It stands for “Socket Secure version 5” and is an enhancement over its predecessors, SOCKS4 and SOCKS4a. Developed to offer improved security, flexibility, and support for various networking protocols, SOCKS5 has become a popular choice for users seeking enhanced privacy and unblocking capabilities.
The history of the origin of SOCKS5 and the first mention of it.
The SOCKS protocol was initially introduced in the early 1990s by David Koblas and later refined into SOCKS5 by Ying-Da Lee. SOCKS5 was first mentioned in RFC 1928, published in March 1996, and further specified in RFC 1929. It was designed to overcome the limitations of previous versions, primarily by adding support for UDP and user authentication. Over time, it has undergone several updates and improvements, solidifying its place as a reliable and versatile proxy protocol.
Detailed information about SOCKS5. Expanding the topic SOCKS5.
SOCKS5 operates at the application layer of the OSI model and acts as an intermediary between clients and servers. When a client requests a connection to a remote server, the data is forwarded through the SOCKS5 server, which then makes the actual request on behalf of the client, hiding the client’s identity. This makes SOCKS5 an ideal choice for scenarios where anonymity and firewall traversal are essential.
Unlike HTTP proxies, SOCKS5 can handle various types of traffic, including TCP and UDP, which allows it to be used for a broader range of applications, such as online gaming, torrenting, and VoIP services. Additionally, SOCKS5 supports authentication mechanisms, adding an extra layer of security to the connection.
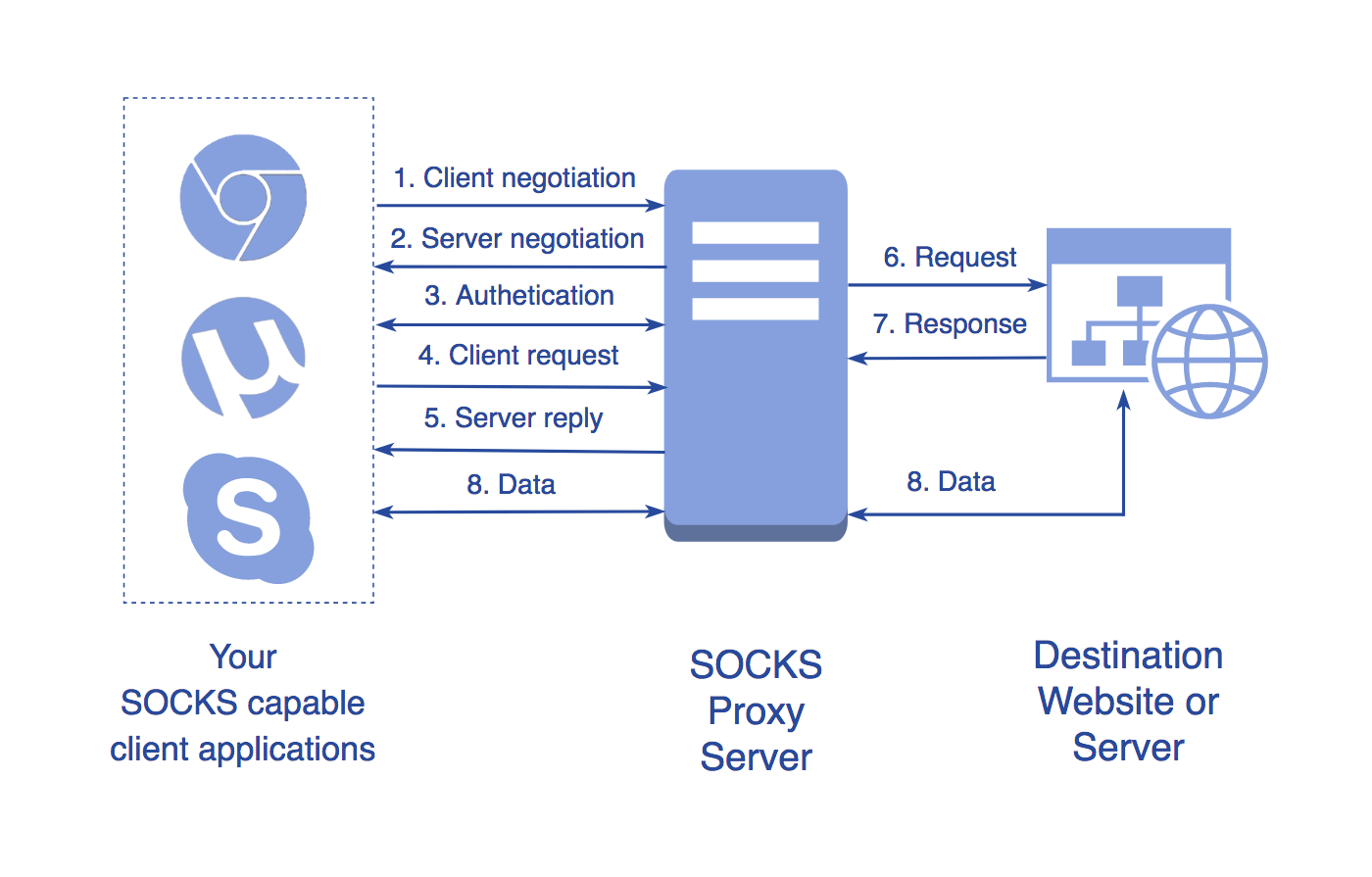
The internal structure of SOCKS5. How SOCKS5 works.
The internal structure of SOCKS5 consists of two main components: the client-side and the server-side.
Client-side:
- When a client application (e.g., web browser, torrent client) wants to access a remote server, it sends a connection request to the local SOCKS5 client.
- The SOCKS5 client then establishes a connection with the remote SOCKS5 server using the specified protocol (usually TCP).
- If authentication is required, the client authenticates itself with the server using username and password credentials.
- Once the SOCKS5 server verifies the client’s credentials (if applicable), the client sends the destination address and port of the remote server it wants to access.
Server-side:
- The SOCKS5 server receives the connection request from the client and validates the client’s credentials (if provided).
- The server establishes a connection with the requested remote server on behalf of the client.
- The SOCKS5 server relays data between the client and the remote server, acting as a transparent intermediary.
- Once the data transfer is complete, the SOCKS5 server sends the response back to the client.
Analysis of the key features of SOCKS5.
SOCKS5 offers several key features that contribute to its popularity and effectiveness as a proxy protocol:
- Versatility: SOCKS5 can handle various types of traffic, including TCP and UDP, making it suitable for a wide range of applications and services.
- Authentication: SOCKS5 supports user authentication, ensuring that only authorized users can access the proxy server.
- Firewall traversal: SOCKS5 enables clients to bypass firewalls and access restricted content, making it a preferred choice for users in restrictive network environments.
- Anonymity: SOCKS5 hides the client’s IP address from the remote server, providing a degree of anonymity for the user.
- Reliability: SOCKS5 is known for its stable and robust performance, ensuring smooth data transfer and reduced downtime.
Types of SOCKS5
SOCKS5 proxies can be classified into two main types based on their authentication methods: authenticated and unauthenticated proxies.
Authenticated SOCKS5 Proxies:
These proxies require users to provide valid credentials (username and password) when establishing a connection. The authentication process adds an extra layer of security, making them more suitable for sensitive tasks and restricting unauthorized access.
Unauthenticated SOCKS5 Proxies:
Unauthenticated proxies do not require any credentials, making them quicker and more straightforward to set up. However, they offer less security and are generally recommended for non-sensitive tasks where anonymity is the primary concern.
Below is a comparison table of Authenticated and Unauthenticated SOCKS5 proxies:
| Feature | Authenticated SOCKS5 | Unauthenticated SOCKS5 |
|---|---|---|
| Authentication | Required | Not required |
| Security | Higher | Lower |
| Suitable for sensitive tasks? | Yes | No |
| Ease of setup | Moderate | Easy |
Ways to use SOCKS5:
- Enhanced Privacy: SOCKS5 proxies can be used to enhance online privacy by hiding the user’s real IP address from websites and services.
- Bypassing Geo-restrictions: SOCKS5 allows users to access region-locked content by connecting to servers in different locations.
- Torrenting: SOCKS5 can be employed to anonymize torrenting activities, preventing IP exposure to other users in the torrent swarm.
- Online Gaming: Gamers can use SOCKS5 to reduce latency and bypass network restrictions, leading to smoother gameplay.
Problems and Solutions:
- Slow Speed: Some free SOCKS5 proxies may suffer from slow speeds due to overcrowding. Opting for premium SOCKS5 services can resolve this issue.
- Connection Issues: In some cases, users may face connection problems with certain websites or services. Switching to a different SOCKS5 server or provider might help resolve this.
- Compatibility: Not all applications or services support SOCKS5 proxies. In such cases, users can use dedicated software or browser extensions that enable SOCKS5 compatibility.
Main characteristics and other comparisons with similar terms.
| Proxy Type | SOCKS5 | HTTP | HTTPS |
|---|---|---|---|
| Protocol | Supports TCP & UDP | Supports only TCP | Supports only TCP |
| Traffic Handling | Versatile | Limited to HTTP | Limited to HTTPS |
| Authentication | Supported | Not typically used | Not typically used |
| Anonymity | High | Low | Medium |
| Performance | Good | Moderate | Good |
Looking ahead, SOCKS5 is likely to remain a crucial component of the proxy landscape, especially in scenarios where versatility and security are paramount. Some potential future developments related to SOCKS5 might include:
- Enhanced Security: New authentication mechanisms and encryption standards could further improve the security of SOCKS5.
- Integration with VPNs: SOCKS5 might be integrated with Virtual Private Networks (VPNs) to provide additional layers of security and privacy.
- IPv6 Support: As IPv6 adoption continues to grow, SOCKS5 will likely evolve to support IPv6 addresses seamlessly.
How proxy servers can be used or associated with SOCKS5.
Proxy servers play a vital role in enabling the functionality of SOCKS5. SOCKS5 proxy servers act as intermediaries between clients and remote servers, facilitating secure and anonymous data transmission. Proxy server providers, such as OneProxy (oneproxy.pro), offer SOCKS5 proxies that can be utilized for various purposes, including:
- Enhanced Privacy: By routing traffic through SOCKS5 proxies, users can protect their identities and online activities from prying eyes.
- Unblocking Content: SOCKS5 proxies can bypass geo-restrictions, enabling access to region-locked websites and services.
- Anonymity: SOCKS5 proxies hide the user’s real IP address, making it challenging to trace online activities back to the user.
Related links
For more information about SOCKS5 and proxy servers, please refer to the following resources:




