Distributed Denial of Service (DDoS) attacks are a type of cyber attack that aim to make a machine, network, or service unavailable to its intended users. Typically, DDoS attacks overload the target system with superfluous requests, making it unable to process legitimate traffic.
The Evolution of DDoS Attacks
The concept of a Denial of Service (DoS) attack has been around since the dawn of computing. However, the first documented case of a DDoS attack dates back to 1999 when a network of compromised University computers, referred to as a “zombie network”, was used to flood a victim’s network with traffic.
Over the next decade, DDoS attacks evolved alongside the internet and technology, becoming more complex and difficult to mitigate. Today, they are one of the most common types of cyber attacks, utilized by both cybercriminals and state-sponsored actors for various reasons including vandalism, extortion, or political motivations.
Expanding the Topic: DDoS Attacks
A DDoS attack works by exploiting the fundamental way in which the internet communicates: the client-server model. In a normal situation, a client (your computer) sends a request to a server (a website), which then responds by sending the requested data back to the client.
In a DDoS attack, this communication model is flooded with illegitimate requests, overwhelming the server’s capacity to handle legitimate ones. The “Distributed” in DDoS comes from the attack being distributed across multiple computers or devices, often forming a botnet (a network of compromised devices) to amplify the attack.
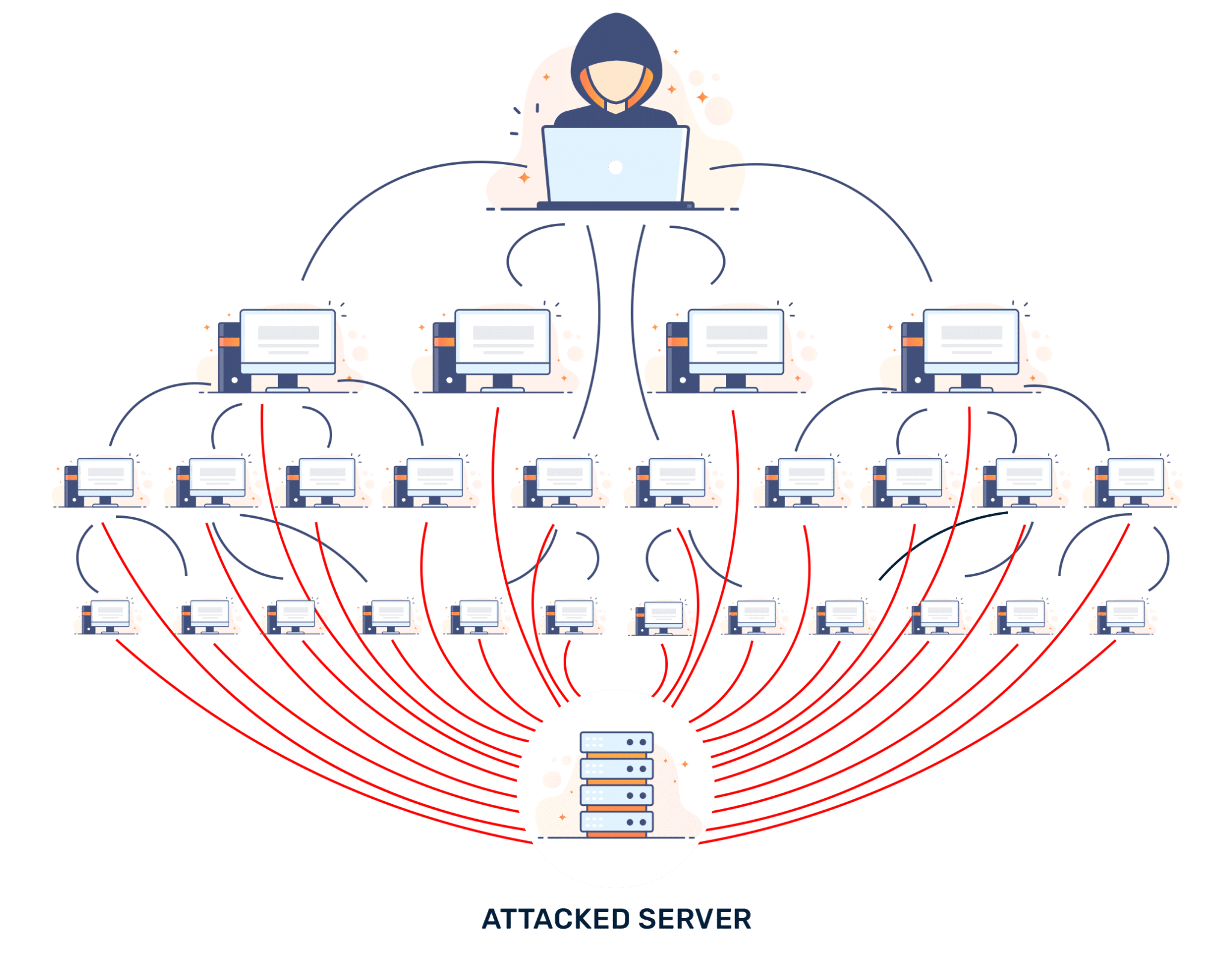
The Inner Workings of DDoS Attacks
DDoS attacks usually consist of three main components:
- The offender(s) controlling the attack
- The machines used to execute the attack (often a botnet)
- The target(s) suffering the attack
The attacker starts by infecting vulnerable systems with malicious software, creating a network of botnets. Once this network is large enough, the attacker can use these machines to generate a flood of network traffic to the target, thereby initiating the DDoS attack.
Key Features of DDoS Attacks
DDoS attacks are characterized by:
- Sudden traffic spikes: They typically involve a significant increase in traffic.
- Multiple IP addresses: Attacks come from multiple sources at once, making them difficult to block.
- Variety of attack vectors: Attackers may exploit different protocols to overwhelm a system.
- Distributed nature: DDoS attacks involve multiple computers targeting a single system, often globally distributed.
Types of DDoS Attacks
There are numerous types of DDoS attacks, but three categories are most common:
- Volume-based attacks: These attacks aim to consume the bandwidth of the targeted site. They include ICMP floods and UDP floods.
- Protocol attacks: These attacks focus on specific network protocols such as ICMP, SYN, and Ping of Death, exploiting weaknesses in these protocols to overwhelm the target.
- Application layer attacks: These attacks target the layer where web pages are generated on the server and delivered to the visitor. They include HTTP floods and slow attacks.
| Type | Examples |
|---|---|
| Volume-based Attacks | ICMP flood, UDP flood |
| Protocol Attacks | SYN flood, Ping of Death |
| Application Layer Attacks | HTTP flood, Slowloris |
Uses, Problems, and Solutions
DDoS attacks are used for various malicious reasons, from simple mischief to political activism, cyber warfare, and commercial sabotage. The problems caused by these attacks can range from temporary service interruption to long-term reputational damage and significant financial loss.
The best way to combat DDoS attacks is through a combination of robust security measures, such as firewalls, intrusion detection systems, and traffic analysis solutions. However, because of the distributed nature of these attacks, it often requires the cooperative efforts of various internet entities to successfully mitigate them.
DDoS Attacks: Comparisons and Characteristics
Comparing DDoS attacks with other similar cyber threats like viruses, worms, and other types of DoS attacks, DDoS attacks have unique characteristics:
- Distributed nature: Unlike other forms of attacks, DDoS attacks originate from multiple sources at once.
- Volume and intensity: The scale and impact of DDoS attacks can be far greater than other types of attacks.
- Purpose: While some cyber attacks aim to infiltrate systems for data theft, DDoS attacks primarily aim to disrupt service.
| Attack Type | Origination | Scale | Primary Purpose |
|---|---|---|---|
| DDoS Attack | Multiple sources | Large | Service disruption |
| DoS Attack | Single source | Smaller | Service disruption |
| Virus/Worm | Single source | Varies | System infection/data theft |
Future Perspectives and Technologies
The future of DDoS attacks will be influenced by the ever-evolving landscape of technology and cybersecurity. As more devices are connected to the internet with the rise of the Internet of Things (IoT), the potential for larger and more potent DDoS attacks grows.
Simultaneously, cybersecurity technologies are developing to counteract these threats. Techniques such as AI and machine learning are being utilized to detect and respond to DDoS attacks more efficiently. Similarly, Blockchain technology is being explored for its potential in DDoS mitigation due to its distributed and resilient nature.
DDoS Attacks and Proxy Servers
Proxy servers can be both a potential target and tool in the context of DDoS attacks. As intermediaries between users and the internet, proxy servers can be targeted to disrupt the internet access they provide.
Conversely, attackers can misuse open proxy servers to amplify DDoS attacks. Therefore, providers such as OneProxy must ensure strong security measures are in place to prevent the misuse of their services and protect their systems from becoming victims of DDoS attacks.
Related Links
- Cloudflare – Understanding DDoS Attacks
- Akamai – DDoS Attack Protection
- Imperva – The Ultimate Guide to DDoS Protection
Conclusion
DDoS attacks pose a significant threat in today’s digital world. By understanding their nature and potential, entities across the internet can better prepare themselves and develop more effective defenses against these disruptive cyber attacks.




