Datagrams represent one of the fundamental building blocks of network communication protocols. They provide a structured format for transmitting packets of data, facilitating efficient and flexible data exchange across various network technologies.
The Origin and First Mention of Datagram
The concept of the datagram can be traced back to the early days of computer networking. The term “datagram” was first coined in 1970 by Louis Pouzin, a French computer scientist. Pouzin introduced the datagram in the design of the CYCLADES network, a pioneering French project that influenced the development of the internet.
The CYCLADES network was significant because it was one of the first networks to implement the end-to-end principle and a connectionless network layer. This network allowed packets, or datagrams, to be sent individually, each finding their own path from the source to the destination.
Datagram: A Closer Look
In the field of computer networking, a datagram is a standalone packet of data that carries enough information to be routed from the source to the destination without relying on earlier exchanges between the source and destination computers. In other words, datagrams are independent packets of data, each transmitted separately.
Datagrams are a primary component of the Internet Protocol (IP), a protocol used for transmitting data across a packet-switched network. Each IP datagram includes not only the payload (actual data) but also header information such as the source and destination IP addresses.
It’s worth noting that datagrams are used in a connectionless mode of communications, known as the Datagram Service model. In this model, each message is treated independently of others. There’s no need to establish a dedicated path before the transmission, unlike the connection-oriented service model where a dedicated path between the source and the destination is established before the data transfer begins.
Understanding Datagram’s Structure and Functionality
An IP datagram consists of two main components:
- Datagram Header: This includes various control information such as the source and destination IP addresses, the protocol used (TCP, UDP, etc.), the total length of the datagram, and other flags for controlling fragmentation and reassembly.
- Payload: This is the actual data that the datagram carries. It’s usually an encapsulated segment of transport-layer data.
When a datagram is transmitted over a network, it’s received by the network interface layer at the destination. Here, the IP header is inspected to determine where to forward the datagram next. Once the datagram reaches the final destination, the payload is extracted and forwarded to the upper layers of the OSI model for further processing.
Key Features of Datagram
The datagram approach comes with several defining features:
- Independence: Each datagram is independent of others. It means they can be sent and received in any order.
- Self-contained: Datagrams carry all the necessary information for routing from the origin to the destination.
- No pre-established path: In a datagram network, there is no need to establish a path before transmitting data.
- Flexible: Since each datagram can choose its own route, this model can be more robust and adaptable to network failures or congestion.
- No guaranteed delivery: Datagram networks do not provide guaranteed delivery or notification of failed delivery.
Types of Datagram
Datagrams can be broadly classified based on the protocol they are associated with. The two most common are:
- IP Datagram: Used in the Internet Protocol, these datagrams form the primary packet format for transmitting data over the internet. They are used by both TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) for data delivery.
- UDP Datagram: These datagrams are a part of the User Datagram Protocol. UDP provides a simple but fast method for the exchange of data over IP networks. It lacks the complexity and overhead of TCP, but also does not guarantee delivery, order, or error checks.
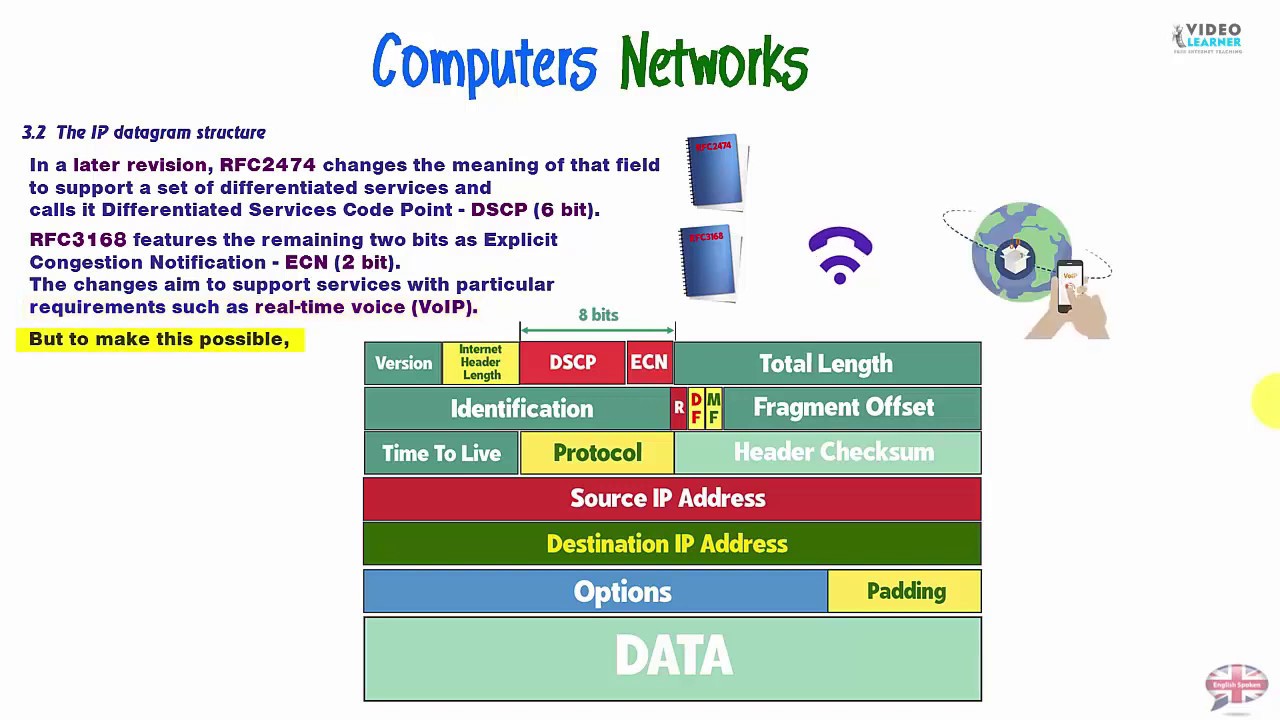
Datagram Usage, Challenges, and Solutions
Datagrams are used across numerous applications in computer networking. They are particularly useful in scenarios where speed is crucial, and occasional loss of data is tolerable, such as live streaming, video conferencing, and online gaming.
However, using datagrams also poses certain challenges. As they don’t guarantee delivery or maintain the order of packets, some datagrams may get lost or arrive out of order. This is typically managed at the application layer, where protocols like TCP ensure ordered, reliable delivery.
For example, if you’re using UDP to send datagrams, you might build additional logic into your application to confirm receipt of datagrams or to reorder them on arrival.
Datagram vs Similar Networking Terms
- Datagram vs Packet: A datagram is a type of packet, specifically a self-contained, independent entity of data carrying sufficient information to be routed from the source to the destination.
- Datagram vs Frame: A frame is a digital data transmission unit in computer networking. In contrast to a datagram, a frame includes synchronization information, error checking, and control data, enabling it to be reliably transmitted to the next directly connected network node.
The Future of Datagram and Emerging Technologies
As networking technology evolves, the concept of datagrams continues to be relevant, particularly with the growth of technologies like the Internet of Things (IoT) and edge computing, which require efficient, flexible data transmission.
Moreover, the development of Datagram Transport Layer Security (DTLS) illustrates a growing interest in secure datagram-based applications. DTLS provides the same security guarantees as TLS (used in secure web browsing) but for datagram protocols like UDP.
Proxy Servers and Datagram
Proxy servers can handle datagrams, serving as an intermediary for requests from clients seeking resources from other servers. They can provide various functions, including security, privacy, and data compression.
For example, a proxy server can allow a client to make an indirect network connection to other network services. A client connects to the proxy server, requesting a connection, file, or other resources available on a different server. The proxy server provides the resource, possibly by connecting to the specified server or serving it from a cache.
In terms of datagrams, a proxy server can intercept them, read and interpret the data, and then perform various tasks based on the datagram’s content. This could involve rerouting the datagram, modifying the data, or even blocking it altogether.
Related Links
For more information about datagrams and related concepts, consider the following resources:




